Mastering Precision: A Comprehensive Guide to Nondestructive and Fully Editable Frequency Separation in Photoshop
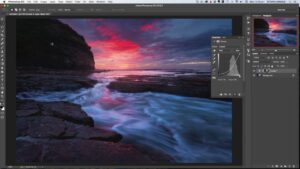
Introduction: Frequency separation is a powerful and sophisticated technique in Photoshop that allows photographers and digital artists to separate the...